Elevating Salesforce Integration with Webhooks: A Security-Focused Guide
In the current digitally interconnected landscape, efficient business operations demand seamless communication between systems. While custom integrations excel in outbound communications from Salesforce to distributed applications, the need arises for systems to send data back into Salesforce in real-time. Enter webhooks, a solution to this challenge.
Understanding Webhooks:
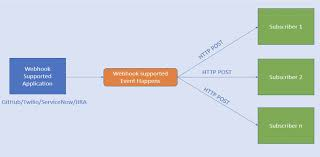
Webhooks represent a hands-off communication method, shifting the traditional integration paradigm. Instead of actively fetching data, webhooks enable a system to send a request to a URL based on predefined events, such as record creation or update. In Salesforce, this involves exposing a URL that passively listens for and handles events triggered by external systems.
Setting Up a Webhook:
Configuring a webhook within Salesforce might seem perplexing initially, as there’s no dedicated area in Setup for this task. However, leveraging Salesforce Sites or Experience Cloud provides a publicly accessible URL to external systems without requiring authentication. Tectonic can assist you.
Security Considerations:
Setting up a Salesforce Site or using Experience Cloud exposes a URL that requires cautious handling due to potential security risks. Several measures can enhance the security of webhooks:
- Access Control:
- Allow only specific IP addresses to invoke the webhook.
- Check for authentication or “secret” headers from known hosts.
- Guest User Profile Permissions:
- Apply the principle of least privileged access, granting minimal necessary permissions to the guest user.
- Input Validation and Sanitization:
- Validate and sanitize data to prevent common types of attacks.
- Error Handling:
- Catch unexpected errors within the handler apex and return a generic 500 status to prevent inadvertent data exposure.
Incorporating these practices strengthens the security of exposed endpoints, mitigating potential risks. However, security is an ongoing process, requiring continuous awareness of potential attack vectors and regular updates to security practices.
Summary:
Webhooks offer a powerful mechanism for real-time data flow into Salesforce. Prioritizing security during webhook setup, following principles like least privileged access, and constant risk assessment are essential. When managed securely, webhooks unleash the potential of real-time communication, elevating your systems to the next level.