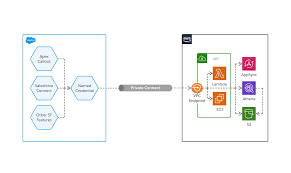
Salesforce is an AWS Partner and a trusted global leader in customer relationship management (CRM). Hyperforce is the next-generation Salesforce architecture, built on Amazon Web Services (AWS). Private Connectivity Between Salesforce and On-Premise Network explained. When business applications developed on Hyperforce are integrated with on-premises systems, traffic in both directions will flow over the internet. For customers in heavily regulated industries such as the public sector and financial services, programmatic access of the Salesforce APIs hosted on Hyperforce from on-premises systems is required to traverse a private connection. Conversely, accessing on-premises systems from business applications running in Hyperforce is required to use a private connection. In this insight, AWS describes how AWS Direct Connect and AWS Transit Gateway can be used in conjunction with Salesforce Private Connect to facilitate the private, bidirectional exchange of organizational data. Architectural overview How to use AWS Direct Connect to establish a dedicated, managed, and reliable connection to Hyperforce. The approach used a public virtual interface to facilitate connectivity to public Hyperforce endpoints. The approach in this insight demonstrates the use of a private or transit virtual interface to establish a dedicated, private connection to Hyperforce using Salesforce Private Connect. Approach AWS Direct Connect is set up between the on-premises network and a virtual private cloud (VPC) residing inside a customer’s AWS account to provide connectivity from the on-premises network to AWS. The exchange of data between the customer VPC and Salesforce’s transit VPC is facilitated through the Salesforce Private Connect feature, based on AWS PrivateLink technology. AWS PrivateLink allows consumers to securely access a service located in a service provider’s VPC as if it were located in the consumer’s VPC. Using Salesforce Private Connect, traffic is routed through a fully managed network connection between your Salesforce organization and your VPC instead of over the internet. The following table shows the definitions of inbound and outbound connections in the context of Salesforce Private Connect: Direction Inbound Outbound Description Traffic that flows into Salesforce Traffic that flows out of Salesforce Use cases AWS to Salesforce Salesforce to AWS On-premises network to Salesforce Salesforce to on-premises network Inbound and Outbound This pattern can only be adopted for Salesforce services supported by Salesforce Private Connect, such as Experience Cloud, Financial Services Cloud, Health Cloud, Platform Cloud, Sales Cloud, and Service Cloud. Check the latest Salesforce documentation for the specific Salesforce services that are supported. Furthermore, this architecture is only applicable to the inbound and outbound exchange of data and does not pertain to the access of the Salesforce UI. The following diagram shows the end-to-end solution of how private connectivity is facilitated bidirectionally. In this example, on-premises servers located on the 10.0.1.0/26 network are required to privately exchange data with applications running on the Hyperforce platform. Figure 1: Using AWS Direct Connect and Salesforce Private Connect to establish private, bidirectional connectivity Prerequisites for Private Connectivity Between Salesforce and On-Premise Network In order to implement this solution, the following prerequisites are required on both the Salesforce and AWS side. Salesforce Refer to Salesforce documentation for detailed requirements on migrating your Salesforce organization to Hyperforce. AWS Network flow between on-premises data center and Salesforce API The following figure shows how both inbound and outbound traffic flows through the architecture. Figure 2: Network flow between on-premises data center and Salesforce Inbound Outbound Considerations for Private Connectivity Between Salesforce and On-Premise Network Before you set up the private, bidirectional exchange of organizational data with AWS Direct Connect, AWS Transit Gateway, and Salesforce Private Connect, review these considerations. Resiliency We recommend that you set up multiple AWS Direct Connect connections to provide resilient communication paths to the AWS Region, especially if the traffic between your on-premises resources and Hyperforce is business-critical. Refer to the AWS documentation on how to achieve high and maximum resiliency for your AWS Direct Connect deployments. For inbound traffic flow, we recommend that the VPC endpoint is configured across Availability Zones for high availability. Configure customer DNS records for the Salesforce API with IP addresses associated with the VPC endpoint and implement the DNS failover or load-balancing mechanism on the customer side. For outbound traffic flow, we recommend that you configure your Network Load Balancer with two or more Availability Zones for high availability. Security For inbound traffic flow, source IP addresses used by the incoming connection are displayed in the Salesforce Private Connect inbound configuration. We recommend that these IP ranges be used in Salesforce configurations that permit the enforcement of source IP. Refer to the Salesforce documentation Restrict Access to Trusted IP Ranges for a Connected App to learn how you can use these IP ranges can to control access to the Salesforce APIs. You access Salesforce APIs using an encrypted TLS connection. AWS Direct Connect also offers a number of additional data in transit encryption options, including support for private IP VPNs over AWS Direct Connect and MAC security. An IP virtual private network (VPN) encrypts end-to-end traffic using an IPsec VPN tunnel, while MAC Security (MACsec) provides point-to-point encryption between devices. For outbound traffic flow, we recommend that you configure TLS listeners on your Network Load Balancers to ensure that traffic to the Network Load Balancer is encrypted. Cost optimization If your use case is to solely facilitate access to Salesforce, you can use a virtual private gateway and a private VIF instead to optimize deployment costs. However, if you plan to implement a hub-spoke network transit hub interconnecting multiple VPCs, we recommend the use of a transit gateway and a transit VIF for a more scalable approach. Refer to the Amazon Virtual Private Cloud Connectivity Options whitepaper and AWS Direct Connect Quotas for the pros and cons of each approach. Conclusion Salesforce and AWS continue to innovate together to provide multiple connectivity approaches to meet customer requirements. This post demonstrated how AWS Direct Connect can be used in conjunction with Salesforce Private Connect to secure end-to-end exchanges of data in industries where the use of the internet is not an option. Like Related Posts Salesforce OEM AppExchange Expanding its reach beyond CRM, Salesforce.com has launched a new service called AppExchange OEM Edition, aimed at non-CRM service providers. Read more The Salesforce Story In Marc Benioff’s own words