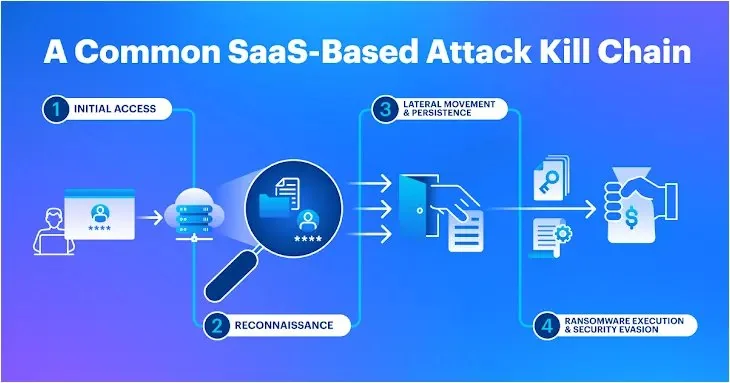
HubSpot recently disclosed a “security incident” where unauthorized access was attempted on several customer accounts. HubSpot is an American software company that provides tools for inbound marketing, sales, and customer service. It was founded in 2006 by Brian Halligan and Dharmesh Shah, and is today best-known for its all-in-one growth platform that helps businesses attract visitors, convert leads, and close customers.. The CRM company detected the incident on June 22, though it was publicly acknowledged six days later by Alyssa Robinson, Chief Information Security Officer at HubSpot. HubSpot seems to have suffered a data breach, but claims to have everything in hand – for now. Robinson stated that the incident involved bad actors targeting a limited number of HubSpot customers, aiming to gain unauthorized access to their accounts. Upon detection, HubSpot promptly activated its incident response procedures and has since been in contact with affected customers, taking necessary steps to revoke unauthorized access and safeguard customer data. HubSpot Hacked With how the statement was worded, it would seem that the attackers, whoever they are, tried to break into the account – but not necessarily succeeded. Still, the company proceeded with the usual practice in case of a cyberattack: “HubSpot triggered our incident response procedures, and since June 22 we have been contacting impacted customers and taking necessary steps to revoke the unauthorized access and protect our customers and their data,” said Robinson. As of Friday, June 28, HubSpot has not disclosed any communication from the hacking group, nor has it specified the full scope of the incident or the exact number of impacted customers. Despite having over 100,000 paying customers and achieving significant financial milestones, such as breaking the billion annual recurring revenue (ARR) mark, HubSpot’s stock price remained stable amid the news, which surfaced through TechCrunch. Ironically, this incident follows HubSpot’s recent announcement of new data protection capabilities for its Smart CRM users. However, it underscores the ongoing challenges faced by major enterprise tech providers regarding cybersecurity. HubSpot says fewer than 50 customer accounts were victims of a breach in late June, all impacted customers were notified and all has been quiet since the initial incident. As of May 2024, HubSpot had more than 216,000 customers, so an incident that impacts fewer than 50 doesn’t seem like a big deal, unless of course you’re one of the accounts involved. What we know: The company is not releasing many details about the incident other than the basic facts. The company said in a June 28 release that it detected a security incident on June 22, 2004, where bad actors were attempting to gain access to customer accounts without authorization. HubSpot’s detection of the breach triggered its incident response procedures and the company notified impacted accounts. On June 28 and again on July 1, 2024, the company reported no further signs of a problem. What’s not known at this time is whether the attack was targeting a specific group of HubSpot customers. Back in March 2022, fewer than 30 HubSpot customers were impacted by a data breach, but all of the impacted customers were in the cryptocurrency business. HubSpot joins a growing list of enterprise tech firms experiencing cybersecurity incidents. While recent arrests, such as that of the alleged ringleader behind attacks on Twilio, LastPass, and Mailchimp, offer some hope, cybersecurity threats continue to evolve with the proliferation of digital devices and AI accessibility. This trend poses new risks, including the misuse of AI technologies like deepfakes, as highlighted by concerns raised by organizations like OpenAI. As businesses expand their digital presence and adopt new technologies, they must remain vigilant against evolving cybersecurity threats to protect sensitive information and maintain customer trust. HubSpot is an American software company that provides tools for inbound marketing, sales, and customer service. It was founded in 2006 and is today best-known for its all-in-one growth platform that helps businesses attract visitors, convert leads, and close customers. Impact for Marketers As marketers, our martech stacks are heavily reliant on cloud-based SaaS applications (like HubSpot) and cloud-based data storage from vendors like Amazon’s AWS and Google Cloud. Even on-premise applications and data are a security risk. The applications running in the cloud and the data stored there are at arm’s length from your data security professionals. More than 80% of the data breaches recorded in 2023 involved data stored in the cloud, according to the Harvard Business Review. Big breaches impacting millions of consumers get a great deal of attention, like those that struck Sony or Target in years past. But smaller, targeted attacks can be devastating to the businesses that have their data exposed, though they fly under the radar of the national press. The number of reported data breaches increased 78% from 2022 to 2023. The cost of the average breach surpassed $4 million in 2023 and is up 15% since 2020. How secure is HubSpot? Is my data secure with HubSpot? All communications between a web client and HubSpot servers are protected using TLS (1.0, 1.1, 1.2) protocol encryption using 2048 bit keys. We also provide customers with the ability to enable Two-Phase Authentication (2FA) to prevent unauthorized use of their portals. Another July Hack One of the most significant data leaks in recent history is reported to have occurred on July 4. The leak, dubbed RockYou2024 by the original poster, “ObamaCare”, on a leading hacking forum, compiled 9,948,575,739 unique passwords into plain text. This means close to ten billion passwords were leaked. That said, the RockYou2024 is primarily a compilation of all previous password leaks and is built on a prior RockYou2021 compilation of 8.4 billion passwords. That means between RockYou2021 and RockYou2024, about 1.5 billion passwords were added to the list. Further, according to the hacker, at least a few of these passwords were cracked using RTX 4090, a tactic that was warned about earlier. According to Cybernews researchers, “In its essence, the RockYou2024 leak is a compilation of real-world passwords used by individuals all over the world. Revealing that many