Government Cloud Authorized and Interoperable Products
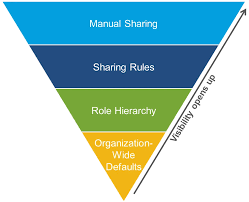
Government Cloud Authorized and Interoperable Products The following table outlines the: Note: Interoperability may be blocked or adversely impacted by network access limitations for U.S. Government customers on restricted access networks such as the Non-Classified Internet Protocol Routing Network (NIPRNet) or other restricted enclaves. Customers are responsible for following safe software deployment best practices and