Security Identity and Privacy Summer 24 Release Notes
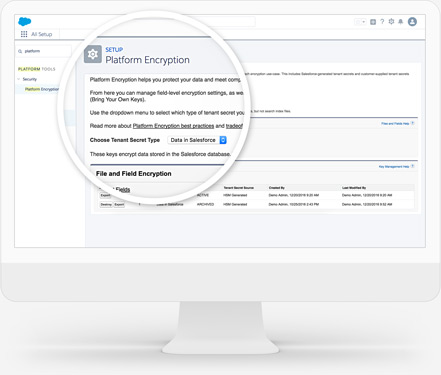
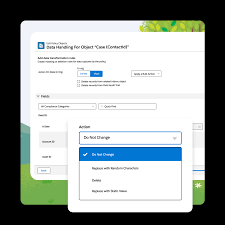
External Client App Manager, OAuth 2.0 token exchange handlers, and Event Log File Browser are each now available in Setup. Also, external client apps now support a bunch of new OAuth flows. Give users access to manage custom domains with a new, more targeted user permission. Create uninterrupted user experiences across Salesforce and custom interfaces