The modern kill chain is eluding enterprises because they are not adequately protecting the infrastructure of modern business: SaaS. Stay Ahead of SaaS Threats.
SaaS continues to dominate software adoption, accounting for the greatest share of public cloud spending. However, enterprises and SMBs alike have not revised their security programs or adopted security tooling designed for SaaS environments.
Security Teams Struggle with SaaS Security
Traditional security controls that CISOs and their teams relied on during the era of on-premise dominance have become obsolete. Firewalls now protect a much smaller perimeter, visibility is limited, and even if SaaS vendors offer logs, security teams need custom middleware to process them into their SIEM.
SaaS vendors define security scopes for their products, but customers must manage SaaS compliance, data governance, identity and access management (IAM), and application controls—areas where most incidents occur. While the SaaS shared responsibility model is universal among SaaS apps, no two SaaS applications have identical security settings.
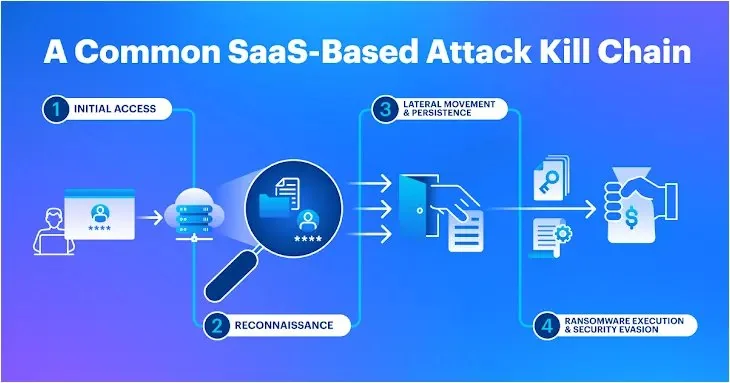
Understanding the SaaS Kill Chain
In the context of SaaS security, the application provider is responsible for physical infrastructure, the network, OS, and the application itself. Customers are responsible for data security and identity management. This shared responsibility model requires SaaS customers to take ownership of components that threat actors target most frequently.
Research by AppOmni indicates that a single SaaS instance typically has 256 SaaS-to-SaaS connections, many of which are no longer in use but still retain excessive permissions to core business applications like Salesforce, Okta, and GitHub. With the multitude of different SaaS security settings and constant updates, security teams struggle to monitor these connections effectively. The number of entry points multiplies exponentially as employees enable SaaS-to-SaaS connections, using machine identities like API keys and digital certificates.
As the attack surface migrated outside the network perimeter, so did the kill chain—threat actors orchestrate their attacks through various phases:
- Initial Access: Compromising an identity in the IdP via phishing, purchasing stolen credentials, credential stuffing, or exploiting misconfigured SaaS tenants.
- Reconnaissance: Post-authentication, attackers search document repositories, source code repositories, password vaults, and communication platforms for privileged escalation entry points.
- Lateral Movement: Attackers move into other SaaS tenants, PaaS, or IaaS, and possibly the corporate infrastructure, seeking valuable data.
- Execution: Encrypting data or delivering ransom notes, while attempting to evade detection.
Case Study: Scattered Spider/Starfraud
In a recent attack by the Scattered Spider/Starfraud groups, a user opened a phishing email and logged into a spoofed IdP page. Through social engineering, the attackers obtained the user’s TOTP token, tricked the MFA protocol, and gained access to Amazon S3, Azure AD, and Citrix VDI. They then deployed a malicious server in the IaaS environment and executed a privileged Azure AD escalation attack, eventually encrypting all accessible data and delivering a ransom note.
Growing SaaS Attack Activity
SaaS breaches, though not always making headlines, have significant consequences. IBM reports that the average cost of data breaches in 2023 was $4.45 million per incident, a 15% increase over three years. Threat actors frequently use tactics similar to those seen in the Scattered Spider/Starfraud kill chain, targeting SaaS tenants and exploiting configuration issues.
Protecting SaaS Environments
- Focus on SaaS Systems Hygiene: Establish a SaaS intake and review process with security requirements, detect Shadow IT SaaS, and monitor SaaS tenants for suspicious behaviors.
- Inventory and Monitor Machine Accounts/Identities: Track machine identities, triage risks, and create policies for account usage, access duration, and monitoring.
- Implement a Zero Trust Architecture: Extend Zero Trust principles to SaaS environments using Zero Trust Posture Management (ZTPM) to prevent unauthorized access and enforce security policies.
With these measures, security teams can gain the visibility and intelligence needed to identify intruders early in the kill chain and prevent breaches before they become devastating.